
to the next level
on real scenarios with increasing complexity.
Thanks to multiple Hacking Games, you can excel both technically
and mentally, thus becoming a higher-level Ethical Hacker.
HOW DOES IT WORK?
HackMeUP divides Hacking Games into levels and classifies them according to the skills required to complete them. At the end of each challenge, participants can map the skills required to the lessons in the CybersecurityUP courses and will have access to explanatory lessons on how to complete the challenge.
ETHICAL HACKING
SOC & THREAT HUNTING
NETWORK & DIGITAL FORENSICS
Thanks to HackMeUP you can

Enhance your attacking skills through exercises with increasing levels of difficulty.

Test your skills on complex attack infrastructures, not just simple virtual machines.

Improve your ability to perform VAPT activities with dozens of scenarios to test

Keep your attack capabilities up to date thanks to the continuous evolution of scenarios

Review the key lessons from CybersecurityUP courses related to the skills needed to pass the test.

Compare your attacking technique with that of the professionals in the field.
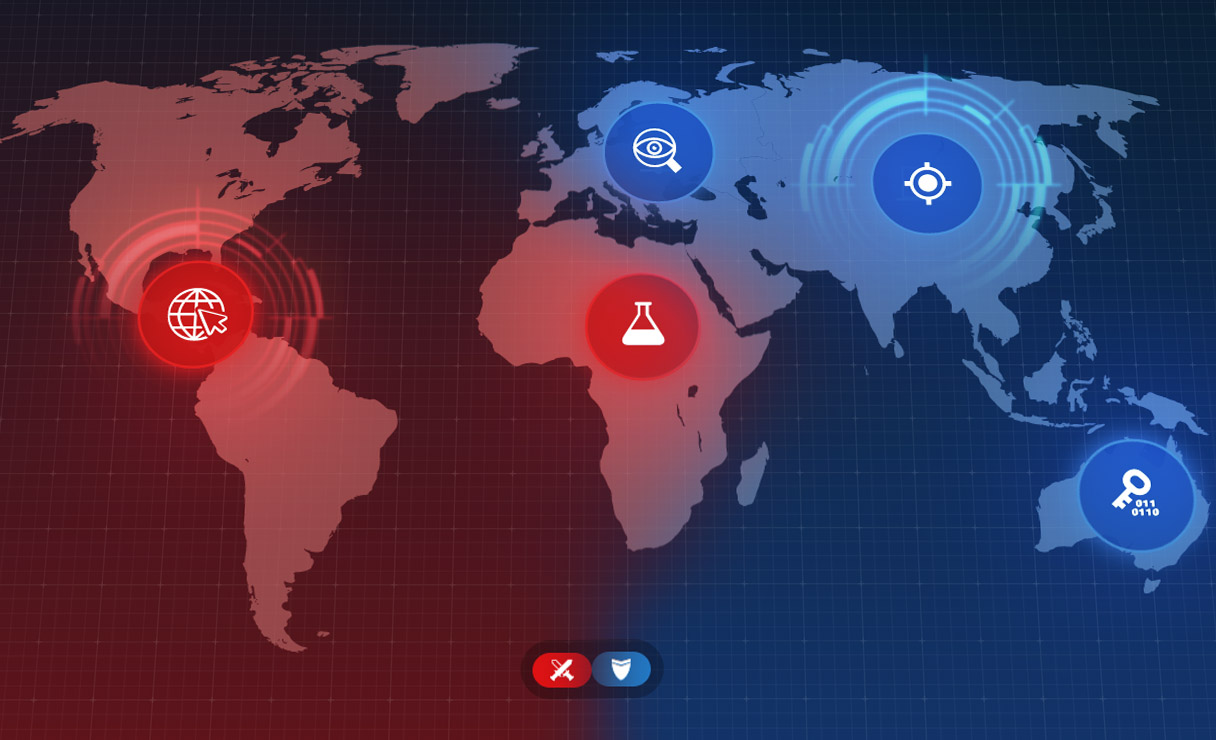
110+ SCENARIOS • 4 CONTINENTS • 5 DIFFICULTY LEVELS • RED & BLUE TEAMS

Offensive Security Operations
Dive into realistic attack simulations. Master exploitation, privilege escalation, and lateral movement across complex infrastructures from Detroit to Tokyo.

Real-Time Threat Detection
Train in high-pressure environments. Learn to monitor and mitigate live attacks in professional SOC workflows, featuring scenarios in Johannesburg, Viterbo, and Lyon.

Proactive Adversary Tracking
Don’t wait for an alert. Use advanced techniques to hunt for stealthy indicators of compromise (IoCs) in our global network, from Atlanta to Nairobi and Oslo.

Post-Incident Analysis
Reconstruct the attack chain. Analyze logs, memory, and file systems to uncover the "how" and "who" behind breaches in scenarios like London or Bogotá.
REALISTIC ATTACK AND DEFENCE SIMULATIONS
The challenges are designed for both Blue Team and Red Team training. Each challenge presents a realistic scenario.
Blue challenges focus on incidents and threats affecting the systems in the scenario.
Red challenges take place in a simulation of a complex infrastructure, with attack opportunities that are exactly those commonly found in such environments.
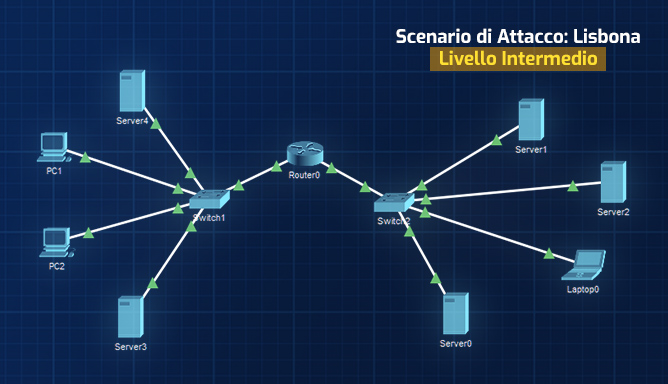

MAPPING CHALLENGES WITH MITRE ATT&CK® TECHNIQUES
Adversarial Tactics, Techniques, and Common Knowledge (or MITRE ATT&CK) is a classification system that describes cyber attacks: all our challenges have been classified using this system, so you can train yourself on specific attack techniques by searching through the MITRE ATT&CK categories.
TRACKING INDIVIDUAL IMPROVEMENT
The challenges are primarily intended as individual training. Participation in each challenge is evaluated based on a series of metrics, both temporal and merit-based, so that each participant can use them to track their technical progress. The metrics are tracked over time and weighted in various ways, so that everyone can have a clear picture of their progress in defence or attack capabilities.
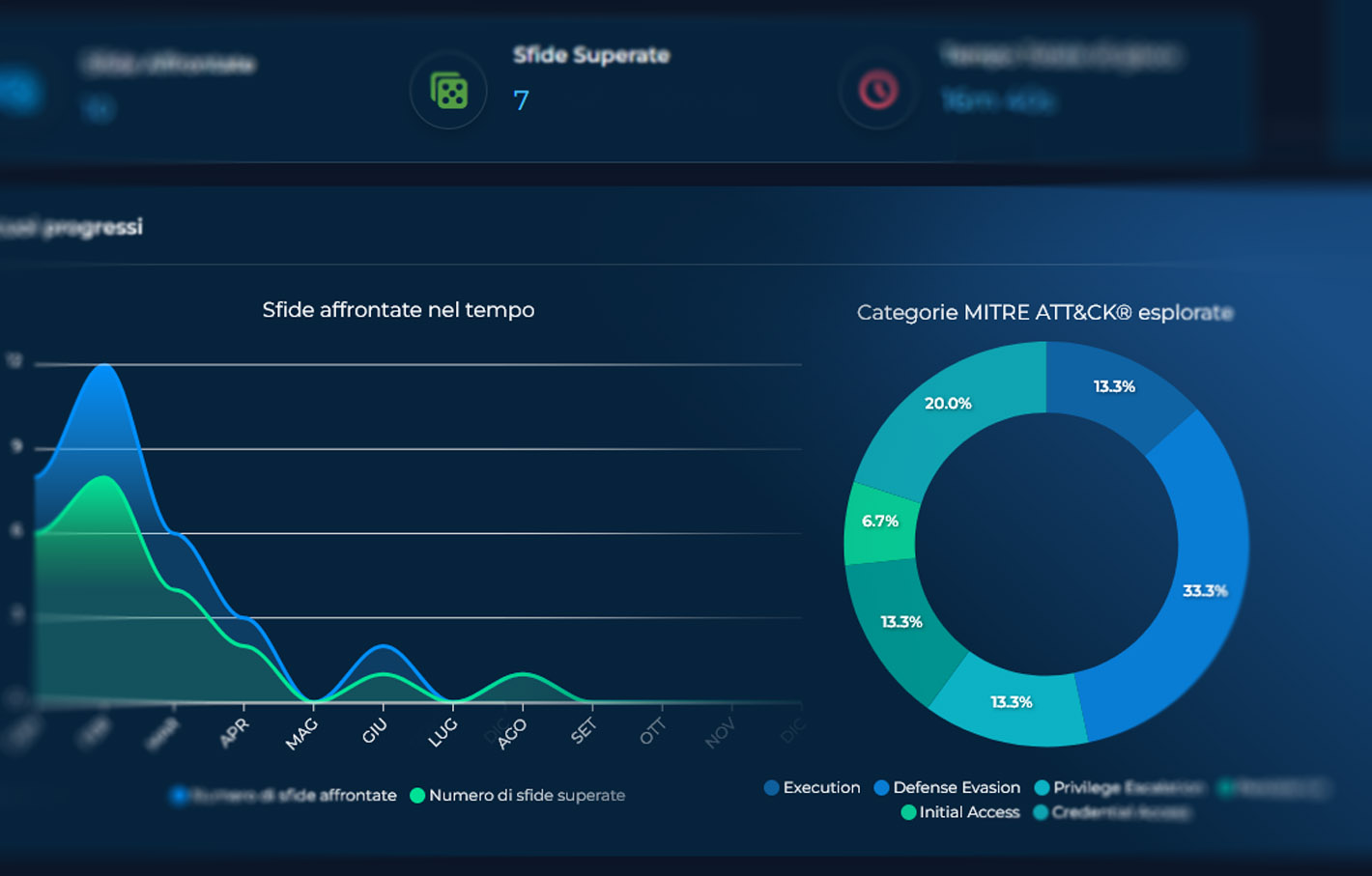

VARIABLE COMPLEXITY OF SCENARIOS BASED ON SKILLS ACHIEVED
Indication of the skills required for each workshop
The different challenges will therefore be classified according to difficulty as well as the techniques to be used: this implies the need for skills for each participant who wants to take on the challenges. No one will be able to mistakenly take on a challenge that is beyond their capabilities, as the skill requirements will be clear.
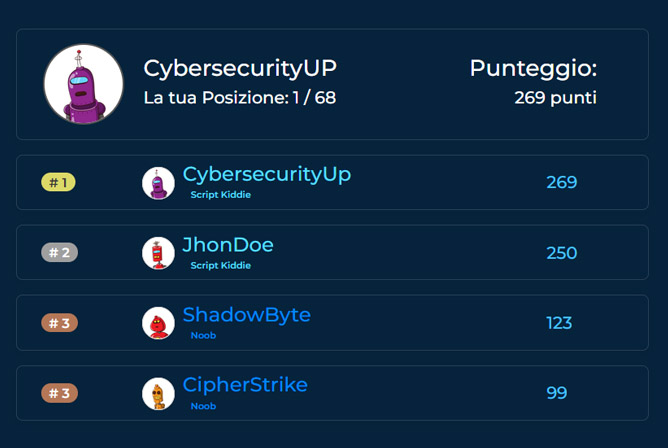
GLOBAL SCOREBOARD TO COMPETE WITH OTHER HACKERS
Individual assessment metrics may be compared with other hackers or defenders who take on our challenges. This constant benchmarking will be a strong incentive for personal improvement. The comparison will naturally be assessed at equal levels of difficulty, but also in absolute terms when participants have taken on many challenges of varying difficulty.
Gamification
Our platform will enable different forms of games among members. Competition, fun and challenges within challenges will be further motivation for growth for everyone, but especially for working groups (Red or Blue) who, together or against each other, will have to face the real world.
Final lesson on solving laboratory problems held by CybersecurityUP lecturers
REALISTIC ATTACK AND DEFENCE SIMULATIONS
The challenges are designed for both Blue Team and Red Team training. Each challenge presents a realistic scenario.
Blue challenges focus on incidents and threats affecting the systems in the scenario.
Red challenges take place in a simulation of a complex infrastructure, with attack opportunities that are exactly those commonly found in such environments.

MAPPING CHALLENGES WITH MITRE ATT&CK® TECHNIQUES
Adversarial Tactics, Techniques, and Common Knowledge (or MITRE ATT&CK) is a classification system that describes cyber attacks: all our challenges have been classified using this system, so you can train yourself on specific attack techniques by searching through the MITRE ATT&CK categories.

TRACKING INDIVIDUAL IMPROVEMENT
The challenges are primarily intended as individual training. Participation in each challenge is evaluated based on a series of metrics, both temporal and merit-based, so that each participant can use them to track their technical progress. The metrics are tracked over time and weighted in various ways, so that everyone can have a clear picture of their progress in defence or attack capabilities.

VARIABLE COMPLEXITY OF SCENARIOS BASED ON SKILLS ACHIEVED

Indication of the skills required for each workshop
The different challenges will therefore be classified according to difficulty as well as the techniques to be used: this implies the need for skills for each participant who wants to take on the challenges. No one will be able to mistakenly take on a challenge that is beyond their capabilities, as the skill requirements will be clear.

GLOBAL SCOREBOARD TO COMPETE WITH OTHER HACKERS
Individual assessment metrics may be compared with other hackers or defenders who take on our challenges. This constant comparison will be a strong incentive for personal improvement. The comparison will naturally be assessed at equal levels of difficulty, but also in absolute terms when participants have taken on many challenges of varying difficulty.

Gamification
Our platform will enable different forms of play among members. Competition, fun and challenges within challenges will be further incentives for growth for everyone, but especially for working groups (Red or Blue) who, together or against each other, will have to face the real world.

Final lesson on solving laboratory problems held by CybersecurityUP lecturers

Why are we different from other platforms?
Because we have devised challenges that take place solely and exclusively in complex environments, therefore in one or more networks and with a variable number of targets (machines and services) that are never singular.
Because you will find specific lessons on how to solve the scenarios. But be careful ! If you look at the solution before you have solved the scenario, you will pay a price in terms of your ranking in the competitions you are participating in.
We will also provide learning references: for each challenge, we will list the required skills and point to the specific module (or section) of our courses where participants can build or strengthen the knowledge needed to solve it.

